
The distributed startup model has become the default, not the exception. Remote teams, global talent pools, and work-from-anywhere cultures offer unprecedented advantages: access to top talent regardless of location, reduced overhead from expensive office leases, flexibility that attracts the best people, and the ability to operate across time zones for round-the-clock productivity.
But this distribution creates a cybersecurity nightmare that most founders severely underestimate.
Traditional security models assumed a defined perimeter: employees worked in an office, behind corporate firewalls, on managed devices connected to secure networks. When something went wrong, IT could physically access the machine and remediate the issue.
Distributed startups have no perimeter. Your team works from coffee shops in Bali, coworking spaces in Berlin, and home offices in Brazil. They use personal devices, connect through public WiFi, and access sensitive customer data from networks you’ve never seen and can’t control.
The statistics are sobering. Cyberattacks on small and medium-sized businesses increased 150% from 2020 to 2023. The average cost of a data breach for companies under 500 employees now exceeds $3 million. For early-stage startups, a single breach can be existential, destroying customer trust, triggering regulatory penalties, and consuming runway in remediation costs and legal fees.
Having worked with dozens of distributed startups implementing security programs from scratch, I’ve seen the patterns: which vulnerabilities get exploited, where founders make costly mistakes, and what actually works to protect distributed teams without killing productivity or breaking the bank.
This isn’t about building enterprise-grade security infrastructure. It’s about implementing practical, cost-effective measures that protect your startup’s most critical assets while enabling your distributed team to work effectively.
Understanding Your Actual Risk Profile
Most founders approach cybersecurity with either paralyzing paranoia or dangerous complacency. The reality requires nuance based on your specific risk factors.
What you’re actually protecting: Customer data (especially PII, payment information, health data), intellectual property (code, proprietary algorithms, business strategies), financial access (bank accounts, payment processors, financial systems), operational continuity (ability to serve customers without disruption), and reputation and trust (often more valuable than any tangible asset).
Your threat landscape: Not all startups face the same risks. A healthcare startup handling HIPAA-regulated data faces different threats than a marketing tool. A fintech company is a higher-value target than a project management SaaS.
Evaluate your risk based on data sensitivity (what’s the worst-case scenario if your database leaked?), regulatory requirements (GDPR, HIPAA, SOC 2, PCI-DSS), target attractiveness (do you hold financial access or valuable IP?), team technical sophistication (are your people security-aware?), and customer expectations (enterprise customers demand security rigor).
The mistake founders make is assuming they’re too small or unimportant to be targeted. Attackers don’t discriminate by company size. They look for easy targets with valuable assets or access to larger networks through supply chain attacks.
The Six Critical Vulnerabilities in Distributed Teams
From analyzing dozens of security incidents in distributed startups, six vulnerabilities account for the vast majority of successful attacks.
1. Weak Authentication and Access Control
The username-password paradigm is broken. People reuse passwords across services, choose weak passwords despite requirements, fall for phishing attacks, and share credentials informally.
In distributed teams where you can’t physically verify identity, authentication becomes your first and most critical line of defense.
The foundation: Multi-factor authentication (MFA) must be mandatory, not optional, for every service that accesses company data or systems. Email, Slack, GitHub, AWS, your CRM, financial tools, and everything else. No exceptions.
Use authenticator apps (Google Authenticator, Authy) or hardware keys (YubiKey) rather than SMS-based 2FA, which is vulnerable to SIM swapping attacks.
Single Sign-On (SSO): Implement SSO through providers like Okta, Google Workspace, or Microsoft Azure AD. SSO gives you centralized control over access, the ability to enforce security policies uniformly, immediate revocation when team members leave, and visibility into access patterns.
For bootstrapped startups, Google Workspace or Microsoft 365 provide basic SSO capability at reasonable cost.
Password management: Require password managers like 1Password or Bitwarden. Generate unique, complex passwords for every service. Store and share credentials securely when team access is needed. Eliminate the practice of passwords in Slack messages or email.
2. Unmanaged Devices and BYOD Risks
When team members use personal laptops, phones, and tablets for work, you lose control over device security, software updates, malware protection, and data retention after they leave.
The ideal scenario: Provide company-owned devices with Mobile Device Management (MDM) software like Jamf, Microsoft Intune, or Kandji. MDM allows you to enforce security policies remotely (require disk encryption, ensure OS updates, install security software), remotely wipe devices if lost or stolen, and monitor for security violations.
The pragmatic reality: Most early-stage startups can’t afford to buy devices for everyone. The compromise is a BYOD (Bring Your Own Device) policy with strict requirements.
Mandatory full-disk encryption (FileVault on Mac, BitLocker on Windows), automatic screen lock after inactivity, operating system updates within 30 days of release, endpoint protection software installed and active, and separation of work and personal data through containerization where possible are all essential components.
Document these requirements and make compliance a condition of employment. Check compliance through quarterly security audits.
3. Insecure Network Connections
Your distributed team connects from everywhere: home WiFi (often using default router passwords), coffee shop WiFi (completely unencrypted), hotel networks (actively hostile), coworking spaces (shared with strangers), and airport WiFi (prime target for attackers).
Every connection is an opportunity for man-in-the-middle attacks, packet sniffing, and credential theft.
The solution: Mandatory VPN usage. Require VPN connections for all work-related activities, not just accessing internal systems. Use enterprise VPN solutions like Perimeter 81, Twingate, or Cloudflare Access rather than consumer VPNs. Configure devices to block internet access unless VPN is active. Monitor VPN usage to ensure compliance.
Modern zero-trust network access solutions are increasingly replacing traditional VPNs, providing more granular control and better user experience.
4. Cloud Misconfiguration
Distributed startups live in the cloud: AWS, Google Cloud, Azure for infrastructure, GitHub for code, Notion or Confluence for documentation, and dozens of SaaS tools for operations.
Cloud misconfiguration is the leading cause of data breaches. An S3 bucket set to public instead of private, an admin panel exposed to the internet, or overly permissive access controls leak massive amounts of data.
Prevention strategies: Implement least-privilege access (everyone gets minimum necessary permissions), regular access audits (quarterly reviews of who has access to what), automated scanning tools (tools like Wiz, Orca, or AWS Security Hub), Infrastructure as Code (manage configurations through version-controlled code), and mandatory peer review for infrastructure changes.
The principle is simple: default to private and restricted, explicitly grant access when needed, and regularly verify that permissions haven’t crept beyond necessity.
5. Phishing and Social Engineering
Technical controls only go so far. The weakest link in security is often human judgment. Attackers know this and target people rather than systems through increasingly sophisticated phishing emails mimicking legitimate services, spear phishing targeting specific individuals with personalized attacks, business email compromise impersonating executives to authorize fraudulent transfers, and social engineering manipulating people into revealing credentials or bypassing controls.
Distributed teams are particularly vulnerable because communication happens primarily through digital channels where verifying identity is harder, people work across time zones with less opportunity for synchronous verification, and isolation makes people more likely to trust unsolicited messages.
Defense in depth: Email filtering with advanced threat protection (Proofpoint, Mimecast, Microsoft Defender), security awareness training (regular, realistic simulations using tools like KnowBe4), verification protocols for sensitive requests (financial transfers, credential resets, data access must be verified through secondary channels), and phishing reporting mechanisms (make it easy for team members to report suspicious messages).
The most effective defense is cultural: creating an environment where people feel comfortable questioning suspicious requests and verifying before acting, even if it means temporarily slowing things down.
6. Insufficient Data Backup and Recovery
Ransomware attacks have exploded. Attackers encrypt your data and demand payment for the decryption key. Even if you pay (which you shouldn’t), there’s no guarantee you’ll get your data back.
Without robust backup and recovery capabilities, a ransomware attack or even a simple technical failure can destroy your business overnight.
The 3-2-1 backup rule: Three copies of your data, on two different types of media, with one copy offsite. For distributed startups, this translates to production data in your primary cloud environment, automated backups in a separate cloud region or provider, and periodic snapshots stored immutably (can’t be deleted or modified).
Test recovery regularly. A backup you can’t restore is worthless. Quarterly recovery drills ensure your backups work and your team knows the process.
Building Your Security Program: The Practical Roadmap
Security programs can be overwhelming. Start with foundations, then layer in sophistication as you grow.
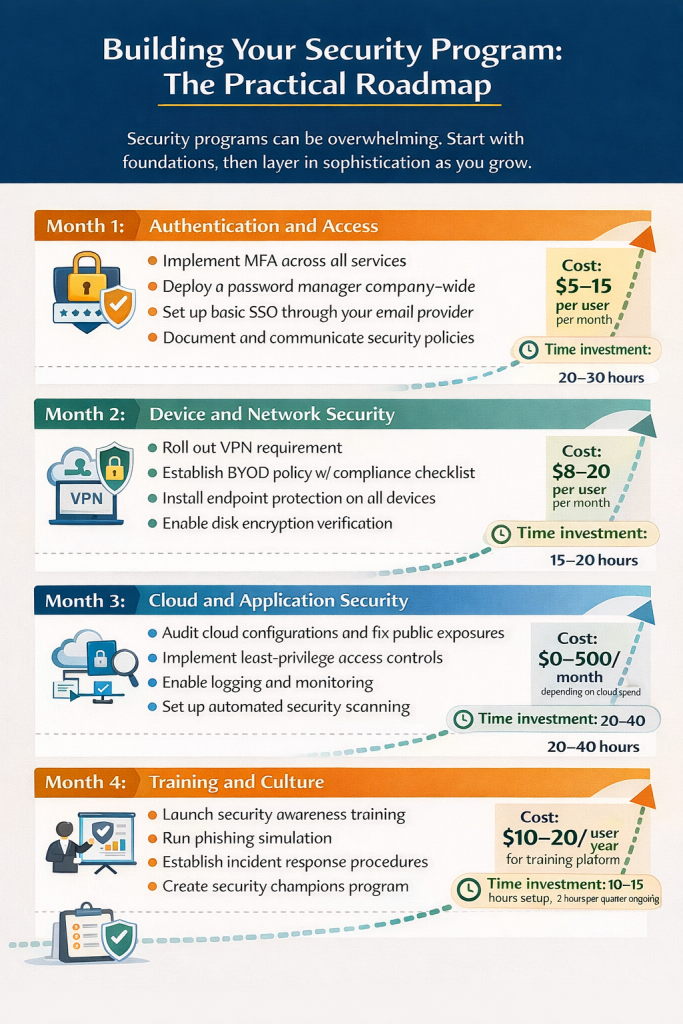
Ongoing: Monitoring and Improvement
Quarterly access reviews. Regular security audits. Continuous monitoring and alerting. Annual third-party penetration testing.
Cost: $2,000-10,000 annually for penetration testing. Time investment: 5-10 hours per quarter.
Compliance Considerations for Distributed Startups
Even early-stage startups face compliance requirements depending on industry and customer base.
SOC 2: Increasingly required by enterprise customers. SOC 2 Type II certification demonstrates you have controls for security, availability, and confidentiality. For distributed teams, this means documented policies, access controls, monitoring, and incident response.
Cost: $15,000-50,000 for initial certification, $10,000-30,000 annually for maintenance. Timeline: 6-12 months.
GDPR: If you have EU customers or users, GDPR applies. Key requirements include data protection by design, user consent and rights (access, deletion, portability), breach notification within 72 hours, and Data Processing Agreements with vendors.
Many GDPR requirements overlap with good security practices.
HIPAA: Healthcare startups must ensure encrypted data transmission and storage, access controls and audit logs, Business Associate Agreements with vendors, and regular risk assessments.
PCI-DSS: If you handle credit card data directly (not through a processor like Stripe), PCI-DSS compliance is mandatory. For most startups, the solution is simple: don’t handle card data directly. Use payment processors that handle PCI compliance.
The Human Element: Security Culture
Technology solves only part of the security equation. Culture determines whether controls actually protect you or become security theater.
Building security awareness: Make security part of onboarding (every new hire gets security training in week one), regular communications (monthly security tips, quarterly all-hands updates), incident transparency (when breaches or near-misses happen, discuss what occurred and what you learned), and recognition (celebrate security-conscious behavior).
The security champion model: In distributed teams, designate security champions in each functional area. These aren’t security experts but interested team members who receive extra training, advocate for security in their teams, serve as first point of contact for questions, and provide feedback on security initiatives.
Champions create distributed security responsibility rather than centralizing it in one overwhelmed person.
Balancing security and productivity: The fastest way to kill security culture is making it so onerous that people work around it. Design security controls that enable rather than obstruct work. When friction is necessary (like MFA), explain why. When simpler approaches exist, choose those over complex solutions.
Cost-Effective Security for Bootstrap Budgets
Enterprise security budgets reach millions. Startups might have a few thousand dollars annually. Prioritization is everything.
Free or low-cost tools: Cloudflare (DDoS protection, WAF), AWS GuardDuty (threat detection), Google Workspace or Microsoft 365 (basic SSO, device management), GitHub security features (dependency scanning, secret scanning), and Wiz or Snyk free tiers (cloud and code security scanning) all provide substantial value.
Where to invest first: Password manager and MFA infrastructure, VPN or zero-trust network access, endpoint protection for all devices, security awareness training platform, and automated backup and recovery.
Total cost for a 10-person distributed startup: $3,000-6,000 annually, or $25-50 per employee per month.
Where to invest as you grow: SOC 2 compliance program, dedicated security personnel or fractional CISO, advanced threat detection and SIEM, penetration testing and security audits, and cyber insurance.
Incident Response: When Prevention Fails
Despite best efforts, incidents will happen. How you respond determines the impact.
The incident response plan: Detection and triage (how do you know something’s wrong?), containment (stop the damage from spreading), eradication (remove the threat), recovery (restore normal operations), and post-mortem (what happened, why, and how to prevent recurrence) are all essential components.
Document this process before you need it. Under stress, people revert to training.
The response team: Incident commander (makes decisions, coordinates response), technical lead (handles remediation), communications lead (internal and external communications), and legal/compliance (manages regulatory and customer obligations).
In small startups, these might be 2-3 people wearing multiple hats.
Communication protocols: Internal communication (how do you alert the team?), customer communication (when and what do you tell customers?), regulatory notification (what are your legal obligations?), and public communication (if needed, who speaks and what do you say?).
Transparency builds trust. Cover-ups destroy it.
The Founder’s Role in Security
Security isn’t just an IT problem. It’s a business risk that founders must own.
Setting the tone: Your behavior signals what matters. If you skip MFA, your team will. If you treat security policies as optional, they become optional. Model the behavior you expect.
Resource allocation: Security competes with product features and growth initiatives for attention and budget. Founders must make hard choices about how much security is enough.
The answer isn’t “perfect security” (impossible) or “minimum viable security” (dangerous). It’s “risk-appropriate security” based on what you’re protecting and the consequences of failure.
Strategic advantage: For B2B startups, especially those selling to enterprises, security is a competitive differentiator. SOC 2 certification, security-first architecture, and robust data protection can win deals against competitors with weaker security postures.
View security as a growth enabler, not just a cost center.
Looking Forward: Emerging Threats and Trends
The threat landscape evolves constantly. Distributed startups should watch several trends:
AI-powered attacks: Attackers use AI to craft more convincing phishing emails, automate vulnerability discovery, and personalize social engineering at scale.
Supply chain attacks: Rather than attacking you directly, attackers compromise vendors or open-source dependencies you rely on, using your trust relationships to gain access.
Ransomware-as-a-Service: The barrier to launching ransomware attacks has collapsed. Even unsophisticated attackers can purchase ransomware kits and target small businesses.
Regulatory expansion: Privacy and security regulations continue expanding globally. Startups operating internationally face increasingly complex compliance requirements.
Staying ahead means continuous learning, regular security assessments, and adapting your program as threats evolve.
Taking Action Today
Cybersecurity for distributed startups isn’t about achieving perfection. It’s about systematically reducing risk to acceptable levels while enabling your team to work effectively from anywhere.
Start this week by implementing MFA on your three most critical services, requiring a password manager for your team, and documenting your current security posture and gaps.
Next month, tackle network security and device management. The month after, focus on cloud security and access controls.
Building comprehensive security takes time, but every improvement reduces your risk and builds the foundation for sustainable, secure growth.
The distributed startup model offers tremendous advantages, but only if you protect the assets and trust that make your business valuable. With practical, cost-effective security measures implemented systematically, you can capture the benefits of distribution without exposing yourself to existential cyber risks.
Connect With Fellow Founders Navigating Security Challenges
Building security programs for distributed teams is challenging, and the landscape evolves constantly. You don’t have to figure it out alone.
At StartUPulse Community, we’ve created a platform where founders share real-world experiences, troubleshoot security challenges together, discuss cost-effective solutions that actually work, and learn from each other’s successes and mistakes.
Whether you’re implementing your first security controls, preparing for SOC 2 certification, responding to a security incident, or simply trying to balance security and growth on a bootstrap budget, you’ll find fellow founders who’ve been there and can help.
Join StartUPulse Community today to connect with founders facing the same cybersecurity challenges, access resources and templates for building security programs, get answers to your specific questions from people who understand startup constraints, and stay current on emerging threats and practical defenses.
Building a secure distributed startup is easier when you’re learning from a community of founders who understand both the technical challenges and the business realities you’re navigating every day.

















